Experience the Juniper AI-Driven Campus of the Future

Ready to see your campus’s future network today? Start here.
The Mist Cloud continues to evolve and expand and now allows you to build an IP Clos network for your campus. Watch as Abhi Shamsundar and Rohan Chadha demonstrate simple management of a live campus environment. This was presented as part of Juniper’s Networking Field Day 27.
You’ll learn
The unique advantages of wired assurance
About an in-depth look at campus full-stack architectures
What a simplified, AI-driven campus fabric deployment looks like
Who is this for?
Host

Guest speakers

Transcript
0:08 we're going to talk about experience the
0:11 campus of the future
0:13 the theme of the today's
0:14 you know session has been continuously
0:16 the full stack the full stack isn't
0:18 complete without our foray
0:19 uh into wired assurance especially going
0:22 into the ai driven uh campuses of the
0:24 future
0:26 the
0:27 just a quick rehash of what we've done
0:29 with wired assurance all all along
0:32 people all of our customers love the way
0:34 missed ap is operated
0:37 you plug in they start beaconing their
0:38 ssid 17 seconds later
0:41 we did the exact same thing going into
0:43 the world of the wired switches as well
0:45 we started the adoption where the claim
0:47 codes uh we started adoption of of
0:49 switches they were using ztp through
0:52 uh zero touch provisioning uh
0:54 and getting to deploy them at scale as
0:56 well we do very well
0:58 with all uh all pieces of anything that
1:01 needs to do with deployment at scale be
1:03 it you know multiple sites across with a
1:06 small branch solution or even a lot
1:08 larger large campus at the deployments
1:11 of the wireless world we brought the
1:13 same thing to the uh wired world too so
1:15 deployment using templatization
1:17 automation uh with with uh with a lot
1:20 more in terms of how can we identify
1:22 devices that come on to your network and
1:25 automatically give them port profiles
1:27 obviously our mainstay for all things
1:29 they do um has always been our ability
1:32 to alert monitor and troubleshoot easily
1:35 so bringing in an automation in to all
1:38 these three pieces was was the key
1:40 pillar for wired assurance as as a as a
1:43 portfolio
1:44 so we spoke about zero touch
1:46 provisioning
1:47 we use the concept of claim codes you
1:50 can claim your switches or you can
1:52 activate thousands of switches all at
1:53 once
1:54 uh and adopt them uh we we speak about
1:57 templatization uh we we speak about
2:00 uh how you can scale how you can
2:03 configure devices at scale and also use
2:06 automation in that fact as well so a
2:08 quick uh refresher on uh what we do with
2:10 dynamic port profiles in in this
2:12 particular example
2:14 there are various kinds of devices that
2:16 come onto your network uh especially
2:17 access switches
2:19 and all of them usually are in bulk you
2:22 provide your access points you provide
2:23 your cameras you provide any of your
2:25 hvac sensors other iot devices
2:28 all configurations across all these
2:29 devices are are usually the same
2:32 on on these interfaces so you let now
2:34 we've brought in the power of dynamic
2:36 port profiles where you say let the
2:38 device
2:39 identify itself as a persona and we'll
2:41 configure it automatically without
2:43 the admin having to go in press a button
2:46 every single time a device comes in to
2:48 say your vlan 2 your speed is 100
2:51 not none of that anymore we can
2:53 automatically detect what device it is
2:55 and we can place them on the profiles
2:58 last piece of it is the wired experience
3:01 on the on the network
3:03 how are you able to down the devices
3:05 that connect on the network how are we
3:06 able to measure stuff
3:08 reid went through a powerful example of
3:11 marvis uh and going through the
3:14 explanation of the wireless was great
3:16 the wired was great and then the van
3:19 where
3:20 was actually the problem how do we come
3:22 to these conclusions on you know uh the
3:25 wireless experience was okay or the
3:26 wired experience was okay is because of
3:28 the amount of telemetry we are able to
3:30 collect
3:31 and provide
3:32 uh these inputs to marvis again
3:35 all of
3:36 all three pieces wired wireless and van
3:39 all all going back to the same ai engine
3:41 and and for that data is key and we
3:43 provide uh these these kind of uh data
3:46 is in into informing these intelligent
3:49 expectations
3:51 so i'll dwell down quickly for a couple
3:53 of more minutes on you know what are the
3:55 advantages of our wired assurance as a
3:57 whole i'll given a few examples of you
4:00 know experiences as a whole
4:02 one of our customers moved from one of
4:05 their radius servers uh to a brand new
4:07 uh radius a different radius server and
4:10 they they are a customer who has over
4:12 1500 sites
4:14 and
4:15 they they just moved uh as a cut over
4:18 from one radio server to the other now
4:21 the sle framework at an org level was
4:24 able to pinpoint exactly the two sides
4:27 on which those those uh new radius
4:29 servers weren't had uh the switches on
4:32 the radio servers weren't added as nas
4:34 clients to exactly say your thousand
4:37 four hundred and ninety eight sites are
4:38 good these two sites are where you where
4:40 it need attention and that's the power
4:42 of bringing in data and also
4:45 condensing them to a point where you can
4:46 consume them easily
4:48 air driven operations we talk about bad
4:50 cables we talk about mtu mismatches
4:52 bring them across you know uh thousands
4:55 of ports uh for example juniper networks
4:58 or
4:58 has about sixty thousand ports we when
5:01 we enabled our assurance on uh we were
5:04 able to bring about exactly 45 parts
5:06 across you know 17 different sites 50
5:10 000 ports to say these are your 45 bad
5:12 cables in there and those those are kind
5:14 of the
5:16 actions that we can provide as an
5:18 administrator so that you know you can
5:20 focus on more things that could be
5:21 productive
5:23 like all things uh
5:25 miss
5:27 every single configuration every single
5:30 stack that we get it's all available in
5:32 automation we have 100 apis and also
5:36 we can you can also work with web hook
5:38 and web sockets for for you to gather
5:40 more information
5:41 in a realistic way if you are consuming
5:43 that way
5:45 best part of it again full stack
5:47 portfolio uh there's one ai engine
5:49 consuming data from wireless wired and
5:51 van so your troubleshooting experiences
5:54 are superior
5:55 let's let's focus on what we want to
5:57 talk about today for especially the
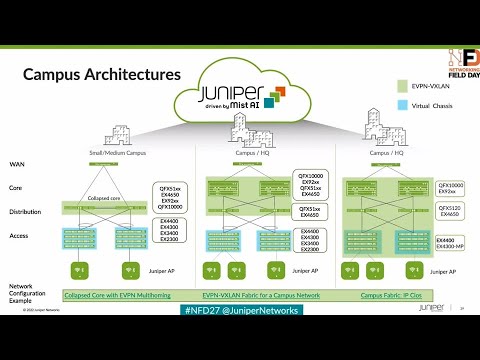
5:59 campus fabric architectures
6:02 we cannot claim that we are a full stack
6:04 solution without us being
6:07 having the ability to
6:10 actually uh talk about campuses and how
6:13 what is our foray
6:15 the the most important uh the the advent
6:19 of evp and vxlan in into the campus is
6:22 recent but also the technology uh by
6:25 itself for the campus administrators are
6:27 new
6:28 it it brings in a level of complexity uh
6:31 where in when you will have to configure
6:34 uh devices and also troubleshoot them
6:36 and that that's a new
6:38 dimension campus administrators have are
6:40 having to deal with
6:41 now everybody wants to move towards
6:44 evpnbxlam because obviously it brings in
6:46 huge amount of benefits for you
6:49 now how do we foray uh into these
6:52 different architectures of juniper as a
6:54 whole we uh we've come out with these
6:56 three architectures and i'll just
6:59 quickly brief through as to what's
7:00 important why we've gone through this
7:03 approach of defining specific
7:05 architectures obviously
7:07 campuses are not one size fits all
7:10 we or we can easily make uh and add
7:12 additions in here but these three are
7:15 guiding uh patterns for you to say which
7:17 would uh fit the bill for a particular
7:20 campus
7:21 the first on your left uh we're talking
7:23 about the evpn multi-homing as we call
7:26 it
7:27 the green blob up there defines where
7:30 the fabric extends across so in in that
7:32 case it's just the collapse code these
7:35 are fit for the smaller architects
7:36 smaller medium architectures your
7:38 distribution device will participate as
7:40 a part of uh you know your access
7:42 devices will still be accessed
7:44 it could be juniper it could be outside
7:47 you can continue to use your existing
7:49 infrastructure at the access and then
7:50 still migrate into
7:52 [Music]
7:53 into fabric by multi-homing your devices
7:56 and creating what we call as uh esi lags
7:59 or ethernet segment identifier
8:01 uh lag interfaces and
8:04 those are best suited for smaller
8:06 architectures or even if you're making
8:07 your 4a uh into
8:09 the world of fabric with minimal changes
8:12 only at your collapse score at that
8:14 point in time
8:16 the second one is uh our campus fabric
8:19 core distribution as the name defines uh
8:22 you can actually
8:23 do the exact same thing if you have a
8:25 larger architecture
8:26 you can still have your axes switching
8:28 outside the fabric they can remain as is
8:31 without any changes to them
8:33 because that's where most amount of
8:34 config changes go into if you prefer uh
8:36 to leave it that way you definitely can
8:39 and still extend your fabric between
8:40 core and your distribution
8:42 and that brings in uh the additional uh
8:45 ease uh to which you you can deploy this
8:48 without actually having to touch
8:50 the most populated part of your
8:51 environment which is the access
8:52 switching
8:54 the right most and the most important
8:56 one i guess which is which is new for us
8:59 which is new for the industry as well as
9:01 we go along is the ability for us to
9:04 stretch fabrics all the way down to the
9:06 axis
9:07 what that brings in is the unique
9:09 advantage of you having uh the ability
9:11 to not only get out at the access but
9:14 also
9:15 uh
9:16 you get all the advantages of evpn vxlan
9:19 uh there's a ton of
9:21 things that we'll also talk about in in
9:23 the next slide but
9:24 one additional advantage that brings in
9:26 is the ability for you
9:29 to actually have security policies
9:32 defined all the way at the edge and try
9:34 and drop traffic closer to the source uh
9:37 it's a unique ability for you to make
9:39 um
9:40 decisions of
9:42 security policy implementation at a
9:44 centralized place like the miss cloud
9:47 and actually have
9:48 security uh
9:50 policy enforced all the way at the edge
9:52 uh the concept constructs of it is
9:54 group-based policy we'll definitely have
9:57 time for it for us to talk about it in
9:59 the in our next uh field day uh but it's
10:02 a unique uh advantage it brings in here
10:05 for today's
10:06 uh session we'll focus on the rightmost
10:09 architecture which is ip clause and
10:11 for one we'll talk about the deployment
10:14 and also talk about what you can do post
10:16 deployment as well
10:18 as a part of the demonstration
10:20 so
10:21 i've already spoken to uh the problem
10:23 statement uh you know you need to uh
10:25 there's a need for stretching mobility
10:27 across you wants a step you want a
10:29 standard space fabric
10:31 which work on evpn vxlan and you would
10:34 like to have multi-homing uh involved as
10:36 well
10:38 what have we done what is miss bringing
10:40 in to actually
10:42 make deployment simple
10:45 in true my style like all things missed
10:48 we went in to the uh we went in with
10:51 actually understanding what the
10:52 administrator is trying to do and how
10:55 what
10:56 and how can we achieve this without
10:58 actually involving all the complexity
11:00 that comes through with the adoption of
11:02 the new technology
11:03 so we we said what what if we already
11:06 have defined the three different
11:07 architectures we said where do you want
11:09 your fabric to be extended so choose one
11:13 we've kind of demonstrated in in prior
11:15 field days we've demonstrated the
11:16 multi-homing as well as the evpn
11:19 um
11:20 ip clause
11:22 the core distribution the topologies
11:24 this one will focus on ip class so you
11:27 you choose the uh topology of your
11:29 choice
11:30 then tell us where your devices reside
11:33 on who which which devices
11:36 are core devices which devices are
11:37 distribution which are access devices
11:41 one thing we will not be able to
11:42 identify is how are they connected
11:44 physically uh if the boxes are still uh
11:47 if the devices are still not uh unpacked
11:50 uh we'll talk about how you uniquely its
11:52 advantage is that you can actually do
11:54 do all of this even without uh
11:58 you can deploy the entire uh network
12:00 even without you having to unbox any of
12:02 your devices as long as you you have the
12:04 activation code with you
12:06 and then you tell us what your networks
12:08 of interest are
12:09 what are your kind of devices that come
12:11 in into the network
12:13 the the most critical piece of it here
12:15 is when we were talking to one of our
12:17 customers
12:19 you know a healthcare customer
12:21 they were talking about the explosion of
12:23 the number of devices that are coming
12:25 into their network and the need for
12:27 segmentation
12:30 how they have to break them uh into vrs
12:33 and that's another advantage you will
12:34 see how you can just define the vlans
12:36 and also if you want to separate them
12:37 into routing tables of their own will
12:39 give you the option to do so but that's
12:42 pretty much it you define the networks
12:44 of your interests and then uh
12:46 and tell us what your physical
12:48 connections are
12:49 and then we'll apply the intent for you
12:51 and
12:53 that would be
12:55 time for us to go into a quick demo
12:58 my name is rohan and
13:01 thank you for passing over
13:03 the demo here
13:05 so here we see um
13:07 obvious spoke about how
13:10 you know easy it is to
13:12 to build the ip class and you all may be
13:14 wondering is it really that easy well it
13:16 is let me let me walk you through what
13:18 we see as we walk into uh the evpn
13:21 configuration here so here you see uh
13:23 there are three different topology types
13:25 for you to choose uh
13:26 you know already spoken about all three
13:28 of them
13:30 well today our focus is campus fabric ip
13:32 class with l3 at the edge
13:35 um
13:36 so so we select one of these topologies
13:38 and you know just give it a name
13:40 and what do we do next we select our as
13:43 numbers
13:44 we select our overlay as we select our
13:46 underlay ais
13:47 here you see
13:49 eventually we can do two byte we can
13:51 also do four byte asn
13:53 no restrictions on that
13:55 uh select your loopback prefix and then
13:57 select your subnet what's the subnet
13:59 really well the subnet is basically uh
14:02 we take care of of the fabric
14:03 connectivity uh you don't have to worry
14:05 about any of those things um you know
14:08 you have you have a three layer topology
14:11 core
14:12 distribution axis
14:14 you don't have to worry about the
14:16 subnetting any of those and we take care
14:18 of all of those things
14:20 so
14:21 um
14:23 moving on
14:26 uh this is this is where you select your
14:28 evpn nodes the
14:31 device is participating in the fabric
14:33 really right
14:34 so select your core devices here
14:38 distribution access
14:42 you have all the information at your
14:44 tips right ready readily available
14:46 um
14:48 if you eventually want to add more
14:50 devices you know you build the topology
14:52 you want to come back and add more
14:54 devices you can expand scale
14:56 click on more switches you'll have more
14:58 switches show up here in your inventory
15:00 and
15:01 you you'll be able to you know add more
15:03 switches to that
15:04 um
15:08 moving on
15:13 um on this page you'll basically be
15:15 configuring your networks and how are
15:18 you going to segment your networks up he
15:20 already spoke about
15:22 uh you know network segmentation
15:24 so basically on this screen you'll be
15:26 selecting your networks uh you can
15:27 create a new network here um you know
15:30 give it a name give the vlan id uh you
15:32 can also you don't have to have a routed
15:35 network in your fabric we also allow you
15:36 to do bridged overlay where you can have
15:39 your gateway on a van device or a
15:42 firewall right uh and you don't have to
15:44 create a network here you can also add
15:46 an existing network let's say you did uh
15:48 you know added add a network uh outside
15:51 of the fabric you wanna import it here
15:53 you can do that uh
15:54 one important feature here that i'd like
15:57 to show you here is you don't even have
15:58 to worry about selecting your ip
16:00 addressing for your for your irb
16:03 svi we take care of all of that stuff
16:05 right you can but if you don't like the
16:07 ips for whatever reason you want to you
16:09 want to change it you can you can go and
16:11 you can you you can statically change
16:13 those ips if you want and then after you
16:14 already spoke about vrf segmentation
16:17 uh you can you know enable your vrf
16:20 share segment uh the vlans per per vrf
16:25 moving on to the next uh page um here uh
16:29 this is the this is the page where
16:30 you'll be basically selecting your ports
16:32 so
16:33 you selected five devices in the network
16:35 you have two cores one distribution to
16:37 access
16:38 all you have to do is just click on
16:39 these devices and click on these ports
16:42 and basically go in and configure your
16:44 ports uh you just want to say hey this
16:46 is my my ge port or it's a it's a a
16:49 multi-gig board
16:50 and
16:52 it's very intuitive uh it's going to ask
16:55 you for for for the number of ports that
16:57 you want and and you can select it
16:59 accordingly right and you can always
17:01 come back and you can edit your ports
17:03 and you can you can change it the way
17:04 you want it to be right
17:06 um so it's as simple as that that's it
17:09 right uh
17:11 moving on we continue this is the final
17:13 view of the topology i can i can click
17:16 here i can see
17:17 this is how my my topology looks like
17:20 this is how i want it do i want to go
17:22 and push the configuration yes i do no i
17:25 don't want to i can go back and make
17:26 changes but in this case we're good
17:28 everything looks good to me we'll go and
17:30 we'll click apply changes and boom
17:33 that's it that's how easy it is to
17:35 config configure your your fabric right
17:38 so um at this point uh we did this exact
17:41 same demo uh when we did uh our previous
17:45 field day uh we said you know you can
17:46 configure your multi-homing in two steps
17:48 all the administrator input was you
17:50 created your vlans you told us how the
17:52 network was connected we we actually
17:55 solved this problem for you
17:57 but uh we we got a response on twitter
18:01 from one of the uh uh from twitter
18:04 saying that's great you you actually uh
18:06 created the fabric in four steps now
18:08 i'll spend 40 hours troubleshooting it
18:11 we took the point he said visibility is
18:14 key what should we do next uh i know
18:17 field day loves live demos i'm gonna go
18:19 ahead and click the next one what should
18:21 we do next how do we
18:23 bring to table
18:25 to make sure troubleshooting is simple
18:27 now
18:28 do i dump all of your show vgp somebody
18:30 and give you a plethora of information
18:33 on click or can i tell you where your
18:36 issues exactly are
18:38 and you can go address that and that's
18:40 where we wanted to bring in the aspect
18:42 of okay what did we give
18:44 the user to actually fiddle with uh the
18:47 most important piece was actually the
18:49 physical connections the rest of it is
18:51 all automated there is very little that
18:53 can go wrong in terms of you uh
18:57 you know configuring the wrong pni or
18:59 configuring the wrong esi id no no those
19:02 things cannot go wrong because all of it
19:03 is automated we've given the control for
19:07 humans for us to say uh go configure the
19:10 ports if there is an error we catch that
19:12 and we bring it to you so if you hover
19:14 over uh rohan uh you will see you know
19:16 uh on the device uh that
19:20 yeah if you you will see that bgp they
19:22 are neighbor
19:24 yeah state is uh is down uh
19:27 and it's also saying that the core two
19:29 is down as well obviously peering is
19:31 down on both ends what is the reason for
19:34 peering being down so let's hover over
19:35 the red line
19:36 the one thing that we gave for us to
19:39 actually uh
19:40 change for us to actually configure was
19:43 the ports and then after telling you
19:45 that whatever port you selected is not
19:47 the port that's a part of the topology
19:49 so let's go ahead and quickly fix this
19:51 uh and then we can come back uh and and
19:53 see how uh how it reflects after and
19:56 also we'll show you a couple more things
19:58 uh in there so let's go ahead right so
20:00 so now that we've seen the problem let's
20:02 go and fix the problem right
20:04 same steps go back
20:06 change the ports
20:07 uh so what was the problem the problem
20:09 was that this is a multi-gig switch
20:13 i i selected a ge port i should have
20:14 selected an mge port
20:18 i'll go and fix that
20:20 that's it
20:22 we make the change apply changes
20:24 confirm
20:26 and while the changes take place now
20:28 while our our bgp tries to come up uh
20:31 let us
20:32 actually walk in and talk about uh an
20:35 important feature here
20:36 uh called uh the connection table right
20:40 um so uh
20:42 yeah this is our topology actually looks
20:44 like uh we didn't go over it but uh
20:48 let's talk about the connection table so
20:49 what's the connection table really so so
20:52 one thing that abby mentioned initially
20:54 was you don't even have to wait for
20:55 these devices to be shipped to you
20:58 you can have the claim codes ready
21:01 once you order these devices you have
21:02 the claim codes you can just go in and
21:04 order uh you know
21:06 down put these claim floats in the in
21:07 the in the system and a device will be
21:10 populated for you and you can build the
21:11 topology so you don't have to really
21:13 wait for the physical devices to be
21:15 stacked so you can build the topology
21:18 download the connection table hand it
21:20 over to your installers and say hey this
21:22 is how the topology needs to be
21:23 connected uh the these this is my mac
21:26 address
21:27 and you you can you can hide all the you
21:29 can hide the the columns you don't want
21:32 you can just say my distribution needs
21:33 to be connected to my core devices like
21:35 this and access the way it is and um
21:39 you know you have the models here
21:41 you have uh the the models for the other
21:44 switches as well here uh it's as simple
21:46 as that uh
21:48 just uh an important uh feature as to uh
21:52 you know
21:53 how
21:55 you can try to fix things that could go
21:57 wrong so so we've taken care of that as
21:59 well
22:00 i mean uh the end goal is you know you
22:02 you put in the hard work to build it you
22:04 don't have to again redraw everything
22:05 well or you hand it over to the low
22:07 voltage guys
22:08 put this excel in front of them and
22:10 hopefully this could be useful for them
22:11 as well in building without errors there
22:14 let's go back into the other piece as
22:16 well
22:17 the other thing uh that we also did uh
22:19 if you go to the access switches yeah
22:21 yeah i'll talk about uh this the
22:24 important uh other important features
22:26 there that we have now uh so you see so
22:29 you go to any device and you click on
22:31 any device you switch insights and
22:33 you'll see
22:34 you'll see the remote shell so
22:37 basically
22:38 we have the remote shell for you
22:39 anything uh if you want to log into the
22:41 device for anything uh as much as we
22:43 would like for you to not do i know all
22:46 of us are uh cli junkies all the way
22:48 inside yeah if you'd like to see it uh
22:50 it's there you can remotely from
22:52 wherever you are in the world yeah you
22:54 can just log in and you can you know run
22:55 any commands you want and you can see if
22:57 your your things are working the way you
22:59 would want or not right
23:01 um uh that is that is a remote shell new
23:04 and improved uh look at switch insights
23:06 so what switch insights really so switch
23:08 insights is basically this is a general
23:11 wide assurance feature um not specific
23:15 to evpn as such and and literally it
23:17 will tell you what's going on with the
23:18 network hey my radio server is only
23:22 my cpu is this my memory is this my it
23:25 is literally doing uh the job of a
23:28 network monitoring tool at this point
23:30 right um
23:32 let's jump to uh access to here right or
23:36 actually i'm going to jump to
23:38 code 2 here
23:40 and look what do we see here my bgp is
23:42 back up i can see in my in my switch
23:45 event so you have everything at your
23:47 tips you don't even have to go back into
23:49 log into the device to check that we'll
23:51 show that to you right
23:53 um
23:54 and and then similarly uh that can go on
23:56 with any other switch as well uh
23:59 of course that is up here as well so
24:01 um
24:05 yeah
24:08 right so let's go back into evpn
24:11 and
24:13 our our topology is fixed our bgp is up
24:17 our network uh
24:20 connectivity is restored
24:21 and and we'll tell you that all of this
24:23 at your fingertips
24:25 you can also look the rx in dx bytes
24:27 what exactly is it it's telling you the
24:29 amount of traffic that's flowing over
24:30 that link and uh
24:32 yeah i think um
24:34 a video won't add anything to that i
24:36 mean yeah at the end of the day the goal
24:38 was for the demo was uh one i know
24:40 techfield likes live demos we wanted to
24:42 make sure we do a live demo uh the
24:44 second piece of it is it's not only easy
24:47 to configure fabrics now it's also easy
24:49 to troubleshoot and pinpoint areas of
24:51 where the trouble is and and make sure
24:54 uh you get them addressed and
24:56 wide assurance is progressing at rapid
24:58 pace and this is our four into the
25:00 campus and that's it thank you thank you





